The military knows how to operate in chaotic situations.
Where should resources be deployed? How should isolated platoons be managed? How should field units and central command coordinate activities when communication lines are broken? How can communications be secured? How can systems be made more resilient?
Many military techniques can be adpated to enhance IoT resiliency.
Military communications or “comms” are activities, equipment and tactics the military uses on the battlefield. They include measurement systems, cryptography and robust communication channels. Military doctrine combines centralized intent with decentralized execution. Four key design principles are applied:
- Field units should respond directly to local issues whenever possible. This allows operations to continue even if communications with central command are broken.
- Intelligence should be analyzed in the field and shared according to its priority. This ensures that bandwidth is conserved for the most urgent communications.
- Build in redundancy because systems will fail.
- Ensure the security of communication channels.
Modifying IoT technology to help first responders
How do these concepts apply to the Internet of Things (IoT)? Consider first responders such as paramedics, police officers and firefighters who assist accident victims. To be effective, they need:
- Secure and dependable access to data
- To download patient medical histories to improve their in-field work
- To collect and analyze sensor data locally even if communications are broken
- To easily upload diagnostic data so the ER crew is prepared for the patient’s arrival at the hospital
- To ensure information is kept secure both at rest and while in motion
How are redundant communication channels maintained? How can first responder teams be equipped to operate autonomously when communication links are broken? How are software apps and network configurations remotely updated to ambulances in motion? How can sensor data be pre-processed for better analysis?
 skilledanalysts.com
skilledanalysts.com Designing the solution
Redundant communication
First responders may encounter coverage gaps between multiple cellular providers as they travel. Cellular aggregation automatically ensures that ambulances stay with the strongest, most robust wireless carrier in a particular area. Ambulances serve as local command units and provide Wi-Fi connectivity to first responders.
A mobile application platform
TheLILEE STSgateway is a mobile IoT solution for first responders. It includes two dual LTE radios, a router, a sensor interface and a software application platform. The platform runs software applications offline or online, depending on the availability of a cell connection.
STS uses dual LTE radios and Wi-Fi 802.11ac for connectivity upstream, communications back to the hospital and downstream for responders and medical devices. A cloud-based provisioning system is used to update network and software settings.
Provisioning applications remotely
Software updates and new applications are deployed while ambulances are in operation. This is accomplished by packaging software applications into a virtual machine container such as VMware App Volumes. These containers are “pushed” from the T-cloud to the STS platform. This saves ambulance downtime involved with manually installing software. Mobile device management (MDM) systems, such as VMware AirWatch deploy mobile applications onto phones and tablets used by first responders.
“First responders deal with life or death situations,” said Ahsan Shah, Global Alliances Manager at Airwatch. “They can access patient information on almost any mobile device with VMware AirWatch.”
IoT devices and sensors
First responder vehicles use several devices and sensors:
- Sensors in the engine provide real-time data and diagnostic trouble codes (DTCs). These self-diagnostics are provided through an on-board diagnostics port, OBD2, to monitor engine temperature, running time and other tuning details for predictive maintenance applications.
- Patient monitors report on a range of health of parameters.
- Digital I/O can plug in any button or on-off sensor, such as an emergency alert button on the dashboard. It can trigger a range of responses, such as starting VoIP or video streaming and sending vehicle location updates.
- Accelerometers/gyroscopes provide crash detection and automated emergency alerts.
- Dashboard cameras monitor the area around the first responder’s vehicle.
- GPS sensors are used for automatic vehicle location and computer-aided dispatch. Geo-fencing alerts can be used when vehicles are out of zone, activating cameras and sensors to alert management.
Fusing sensor data
Multiple sensor data streams are “fused” in real time with STS in the ambulance to provide contextual insights. Locally fusing and analyzing sensor data in the ambulance gives first responders the insights they need to give victims better care. Resiliency improves. Bandwidth needs decline.
A door sensor in the ambulance, for example, cannot tell by itself whether a patient is inside or not. STS combines inputs from door sensors with occupancy and pressure sensors on the stretcher to confirm a patient’s position. It can even initiate a live video stream of the patient from the ambulance to the hospital.
 skilledanalysts.com
skilledanalysts.com Security
First responders can be authenticated with passwords and two-factor authentication. But how do you authenticate an IoT device?
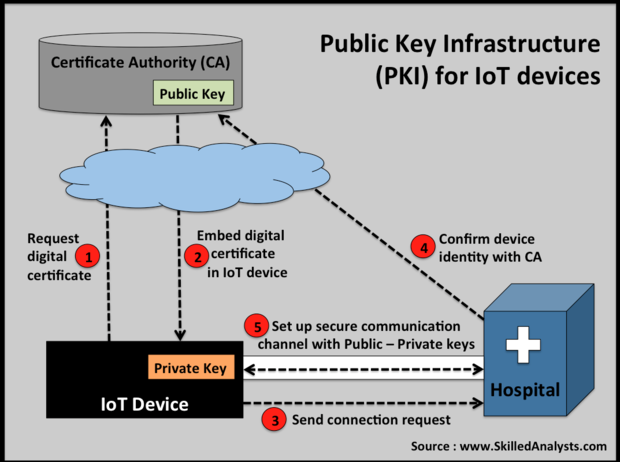
Public key infrastructure (PKI) offers a solution. Devices are issued a digital certificate once they’ve been authenticated. This software certificate consists of a public and a private key. It’s embedded in the IoT device. A certificate authority (CA) digitally signs and publishes the public key associated with an IoT device so that the device can be remotely authenticated.
Once the hospital has authenticated the device, a secure communication channel is set up with the public and private keys. This channel is used to receive data from the device and to send it updates. Symantec and DigiCert provide Public Key Infrastructure for IoT applications.
Techniques refined by the military over decades have a lot to offer IoT designers. The LILEE STS gateway incorporates these concepts, enabling first responders to provide better care.
This article is published as part of the IDG Contributor Network. Want to Join?
